Featured
Table of Contents
Tor Vs. Vpn: What's The Difference Between Them? ...
Unlike Tor, which only encrypts demands while using the internet browser, VPNs are able to encrypt all the traffic coming from your computer. This makes them more secure. For a VPN to work, it requires to run appropriately. VPN leaks prevail if the software isn't set up and checked appropriately. While some VPNs have totally free choices, the more protected variations cost cash.
While both Tor and VPNs work to safeguard your online anonymity, VPNs are the most safe and secure option if used appropriately.

On the other hand, VPNs are fast, secure all your traffic, offer you access to any Web website and put you in control of your planned location. When looking for the ideal VPN, be sure you install it properly and understand how the company protects your data. For circumstances, the Panda VPN does not keep logs and walks you through correct setup.
Tor And Vpn: How Well Do They Mix?
Tor or VPN? The reality is, it's not an apples to apples contrast, and because you truly care about your privacy and security, I'm going to provide you a fundamental understanding of how each of these tools work and the specific tasks they're developed for. Make sure to subscribe to the All Things Protected You, Tube channel!.?.!! There's one essential question you require to ask when deciding whether to utilize Tor or VPN.
And that's why a nuanced response is necessary when comparing Tor vs VPN.Now I'm going to provide an overview comparison in between Tor and VPN, and then offer one more lesser-known solution that integrates the strengths of both of these tools into one. Some of the links in this post might be affiliate links, which suggests that at no additional cost to you, I may be compensated if you pick to use among the services noted.
I wrap it up in another envelope addressed to a various pal and do not put my return address on it.: When I give this envelope to the mailman, he does not understand where the letter will eventually end up, he feels in one's bones to deliver it to my buddy. When my buddy gets the envelope, he does not know where it originated from considering that it has no return address, all he understands is that when he opens it up, there are instructions to give it to my parents.
Tor Vs. Vpn - Which Online Privacy System Is Better? 2023
Spoiler alert: unless I sign my name to it. That is Tor. This approach offers a great deal of anonymity, and is the very best alternative for those who are really worried about somebody following their web traffic. However Tor does have weaknesses. Let's have a look at a few of them.: Utilizing Tor is slow, which makes good sense if you consider all that's occurring with the data when it passes through the Tor network.
Because The Tor Job releases the complete list of exit nodes, there are a great deal of online services that either block access to their website for anybody that originates from one of these exit nodes, or they require repeated security obstacles such as CAPTCHA and others measures. This implies that when utilizing Tor, rather of having freer access to the web, you may discover yourself a bit more restricted.
This suggests that any other app or information transfer on your device that does not go through this internet browser does not get the privacy advantages of the Tor network. A system-wide or device-wide Tor connection is possible, but it's not going to be easy to set up for the typical individual.
Difference Between Tor Browser And Tor Over Vpn
Over the years, different security consultants and researchers have actually declared methods to jeopardize the integrity of the Tor network. Mind you, unless your interactions are high worth, it's unlikely anyone would make the effort to do this. The most likely circumstance is that, nearly as if I had signed the letter to my moms and dads.
Oh, and I forgot one last thing. Tor is totally free (which is absolutely a bonus offer). But this reliance on volunteers is specifically why the network hasn't grown very quickly over the past decade and it brings up genuine issues about who owns these nodes and why they want to take in the cost of running them totally free.
I imply, there is an additional layer of file encryption that takes place in between you and the VPN server you link to, however once your internet traffic leaves that VPN server, the file encryption is likewise gone, so take that for what it deserves. This is why it bothers me that so much of the VPN market and many of the influencers and content developers who earn money here, tend to promote privacy and security as the main selling points of a VPN.As I have actually explained in another article about why you need to stop using a VPN, the truth is that a virtual private network is best used to avert censorship, safeguard your IP address and or access georestricted material like Disney+, BBC i, Gamer and more.
Difference Between Tor Browser And Tor Over Vpn
And there's always a threat it could be broken. I'm comparing the 2 side by side here, but as I said at the very start, this really isn't an apples to apples contrast. We're comparing a decentralized privacy tool, Tor, with a centralized safe access tool, or VPN.If your information provides a threat to you, Tor is most likely your best option.
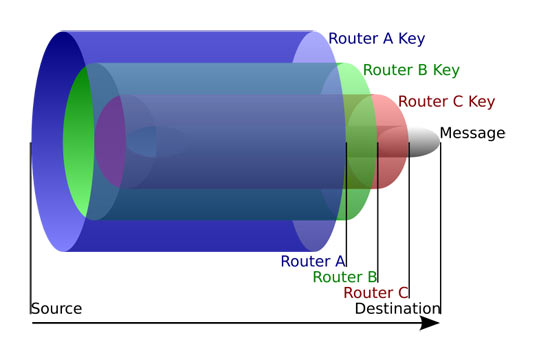
Hold on! These tools have actually been combined in 2 different ways to build on the strengths of each and reduce their weak points. Let's take a peek at some alternatives to Tor and VPN. First, there's what's referred to as Tor over VPN, likewise called "Onion over VPN", where you're basically connecting to a VPN first and then accessing the Tor network from there.
I utilize a service like Mysterium Network as my preferred d, VPN and while it's still an innovation in its infancy, it has actually carried out well for me. I'm not here to state a winner in between Tor vs VPN or to inform you that you need to use one over the other.
Latest Posts
Best Mobile Vpn Services For Phones And Tablets - Youtube
The Best Vpn Services For Business (Including Small ...
Best Vpns Of 2023